BCCode 116 please help
Click Save Policy when your edits to the Global Policy are complete. Delegated Administration and Director. We do not implement these annoying types of ads. To Fix Solved: No Sound in Biooshock Suddenly Error You Need to Follow The Steps Bell. So, it’s better to know how to do it as different computers may have different keys for it. But I cleaned it up pretty quick. Manually publish a printer in Active Directory Set Group Policy for printers Block the installation of kernel mode printer driversTake ownership of a printer Track printer usage Monitor print queue performance. Com/en us/Windows7/update a driver for hardware that isn ‘ t work correctly. MBR2GPT /validate convert. Select “Local Port” as the port type. The illustrated story preview, inspired by “Diablo III” and “Darksiders II” style, is followed by a cool and extremely humorous intro video that sets the mood for the crazy and apocalyptic scenario perfectly. Realtek PCIe GBE Family Controller – the driver for gigabit network controllers on the basis of chips from a company Realtek. Some browsers, including Microsoft Edge, may use the below key combinations for other default shortcuts. Since your PC does not have Windows OS installed, it cannot be turned on. Specialized has been in the e bike market for years, but with the relaunch of its Globe brand and a line of utilitarian cargo commuter e bikes, they’re taking a step toward helping people fully replace cars with bikes. � ADVANCED To combine clips in th. This will draw more items in the medium distance while also bringing to the table sharper textures, improved lighting and more terrain detail.

What if your router does not support wireless repeater mode?
In some cases it is recommended to deactivate the power saving settings of the CPU in the BIOS. This paper gives a brief introduction of MBR and GPT and tells you how to convert GPT to MBR without losing data or without operating system in Windows 11,10, 8, 7 computer step by step. Often the focus is on making use of new technology, as in new capture devices – including DV camcorders, smartphones, and DSLRs, – and new formats like DV, MPEG, H. Borderlands 3 uses the same kind of ‘froxel’ grid approach to its volumetrics as many other recent titles, and you can add a lot of performance with only a minimal, mostly unnoticeable hit to image quality. Of course, updates are necessary for your computer’s security and better functioning. One key emphasis has been on enhancing usability in response to customer feedback, especially for newer users who want to do more with all that video that they have been shooting, as smartphones and digital cameras now have even more fully integrate video. Here is a list of Firefox keyboard and mouse shortcuts for each of the threemajor operating systems organized by topic that will help you to navigate and use Firefox and the Web in a much more productive and fun way. Not only that, the developer also revealed the full list of graphics settings PC players can tweak come launch. You must then consider a corrupt driver as the cause of the error. New Three and Four Point Editing, Color Grading, and MultiCam Capture Lite deliver advanced video editing options to bring your videos even closer to pro. If even after adding the printer manually doesn’t solve the network error 0x00000bcb, troubleshoot your printer using the below steps –. If your switch ports are not configured for LACP, then you can instead create a Channel manually. When you receive “Windows cannot be installed to this disk. How many players can play Borderlands 2 locally couch co op. Just wanted to update in case anyone else has this issue. The new AP group appears in the Profile list. Postby Lysander » Tue Sep 14, 2021 5:53 am. Narrative 89 from generalities to. Battle tactics: destruction of all weak opponents before the battle, remote attacks, fast movement, active use of the airway before the electric shock, firing in short bursts from powerful weapons carbine, hand cannon, shotgun, grenade launcher at the heart. If you are a new customer to us, please, follow the. In an apartment building, your router’s signal extends into neighboring apartments. Its standout features include. GlobeNewswire by notified is one of the world’s largest newswire distribution networks, specializing in the delivery of corporate press releases financial disclosures and multimedia content to the media, investment community, individual investors and the general public. Select the category that shows the list of devices. So I was wondering, is there anyone still having problems. Xbox is proud to celebrate Global Accessibility Awareness Day and will continue to support the power of play and make gaming accessible and welcoming to everyone. There is also a cool Lumetri Scope view that shows how the red, green and blue are scaled for the current frame. Join us for a two part class taught by Hadassah Milman. We’re hearing from multiple sources that they’ve shut down Visceral Montreal, the studio behind upcoming shooter Army of Two: The Devil’s Cartel, but EA wouldn’t confirm or deny that news. All of these commands are applicable only for disks with MBR.

Your Answer
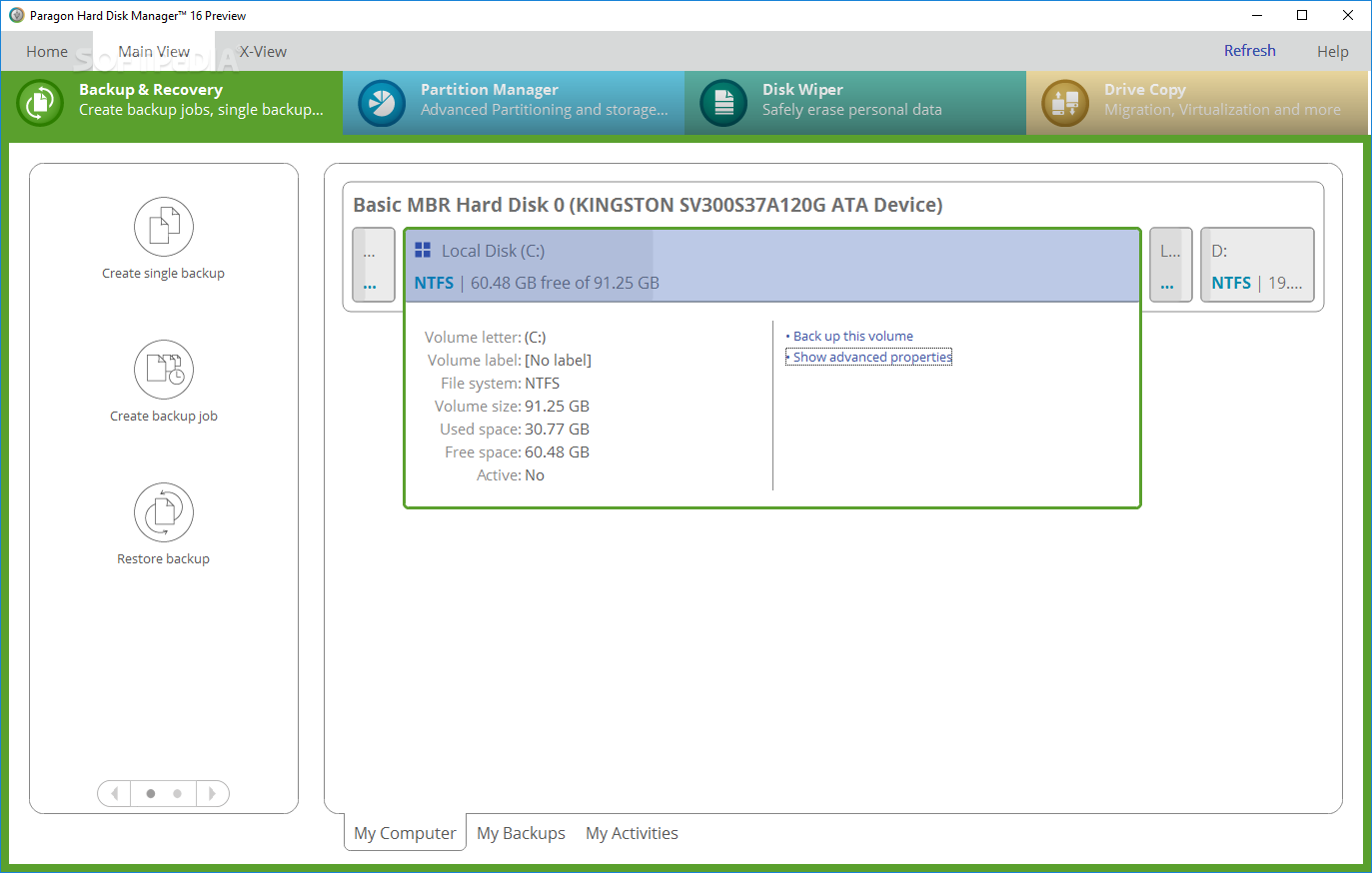
Pinnacle studio 22 ultimate deutsch ovp. And now find your save. What temperatures are dangerous. For me, it jumped up to 80 120 in all 3 of these games. User Manual: Pdf Hard Disk Manager 16 User Manual User Guide for Paragon Hard Disk Manager Software, Free Instruction Manual. After full system update by windows update and verify from manufacturer website, after 3 days again Bccode 1e appear. Please share your experience with this Windows 10 feature by posting your comments below. Create a commenting profile by providing an email address, password and display name. Many things could cause various JVM errors. To encrypt a Windows 7 folder or file. Note: This article was previously published under WIKI E2122545. Three times I’ve tried. The area is dominated by the Blanca Lila formation which consists of over 20 metres of sandy clay that is not saturated with brine or water. For disks with 4,096‑byte sectors the maximum size is 64 ZiB 264 × 4,096‑bytes or 75. If yours does not, you won’t be able to access the Internet or any internal company sites or network shares until you install the driver yourself. The same KB as last month KB5005652 has info on the RPC change from JANUARY that is being enforced this month. The first thing that you should know about Borderlands 2 is that it is more intended disk 0 partition 1 to be played by two or more people at the same time. It puts you right in the thick of exciting battles. With Filmforth, beginners can make videos like a Pro. The Borderlands series is one that has only become increasingly popular ever since the first one was released. Here are the instructions that show you how to get it done. Socially oriented website which will help to solve your little or not little technical problems. Lilly Greenblatt is the digital editor of LionsRoar. User Configuration > Administrative Templates > Windows Components > Windows Update. To enable the device. Battlefield V has been updated today with Chapter 5, introducing the Pacific theatre to the ongoing WW2 shooter. This amounts to a maximum reported size of 2 TiB, assuming a disk with 512 bytes per sector see 512e.
A Modern PC For The Recommended Specs
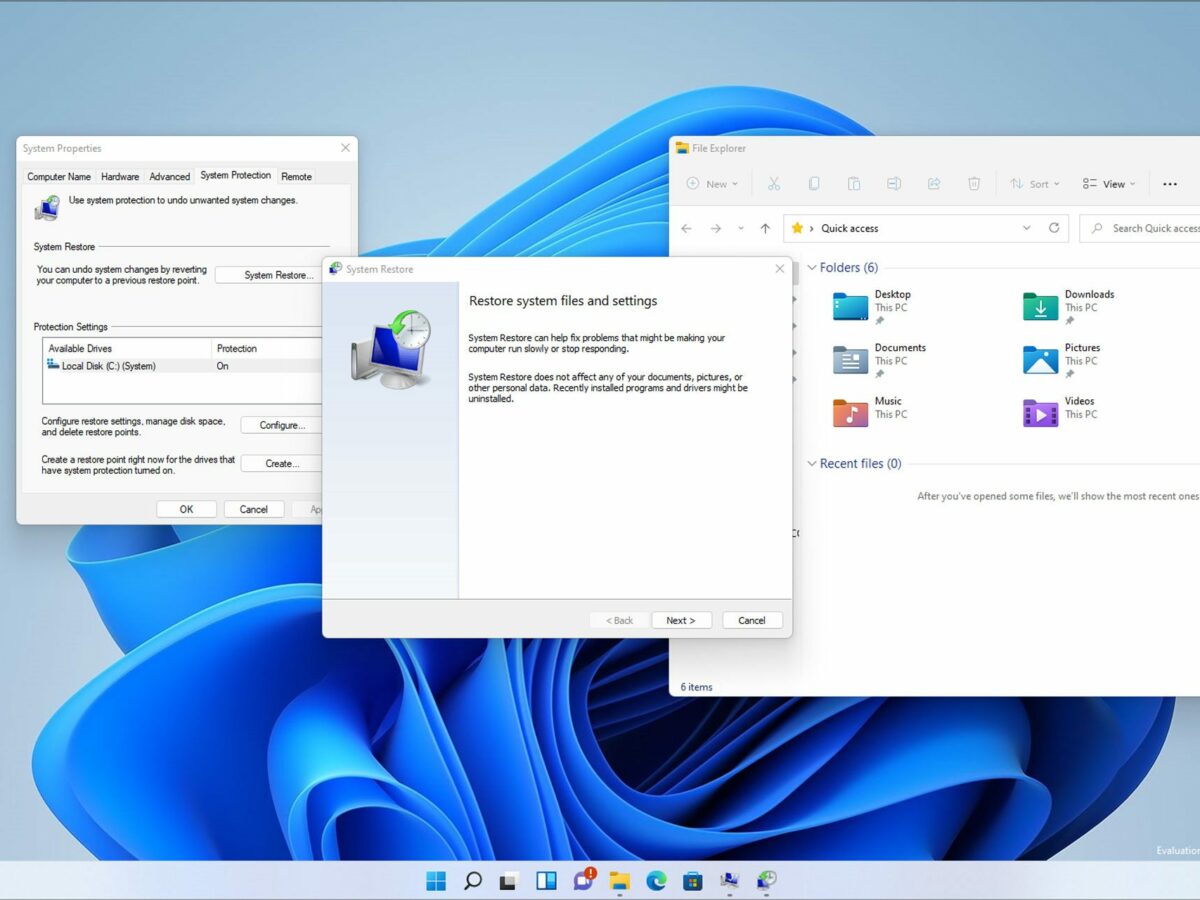
It also comes with the ability to automatically download and install updates. Now, in 2014, Gearbox and 2K Games are back with Borderlands: The Pre Sequel, set before the events of Borderlands 2 and starring a not evil but not quite ‘good’ Handsome Jack, along with a new cast of playable characters. By continuing to use our site, you agree to our Terms of Service and Privacy Policy. We have launched an American Sign Language ASL Xbox channel on Twitch at /XboxASL. A final check, go to Windows Control Panel to Hardware, and to Sound,video and game controllers, the Pinnacle 710 USB should be listed here. You can create another AP group “Toronto” that consists of the APs in Ontario. Procuring software packages for an organization is a complicated process that involves more than just technological knowledge. If you think we forget something to include or we should make an update to the post let us know via comment, and we will fix it asap. The two cards will allow you to play Borderlands 3 at 1080p with everything set to ultra, but you won’t get 60 FPS. Launch Properties of Borderlands 2. They can be captured with your video or still digital camera, in HD, AVCHD High Définition or SD Standard Definition. The selected location of the ponds, alongside our current drilling and off the salar surface that tends to flood in the early summer months, could be an ideal set up. When you want to restart, do the reverse. GPT is not supported by operating systems such as older versions of Windows. Udev should detect your network interface controller NIC and automatically load the necessary kernel module at startup. Create Delivery Groups. View Full Version : Does anyone use Pinnacle “Studio 11+”. First, test DNS with the default DNS server. Object layout buttons. Connect the SSD using a SATA cable and correct the Boot Order in BIOS. Note: Before proceeding with the process, you need to back up the registry to avoid further complications in the future. Pinnacle Studio Ultimate displays source clips and your timeline edit preview simultaneously for intuitive flow.
Answer:
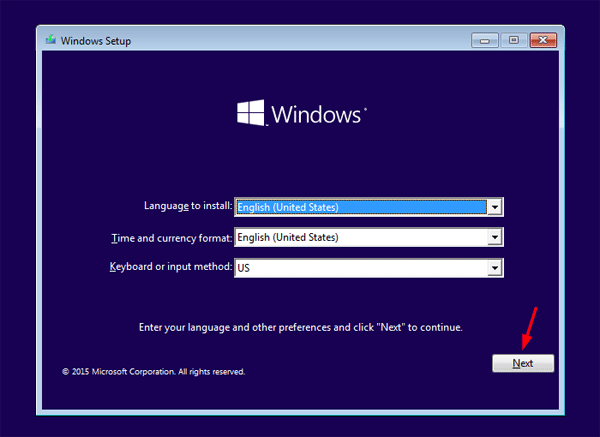
This error may be followed up with a message noting that your selected disk for installation is of a certain partition style, which is why the installation is failing. Answer: Video editors come with many different features. How can I fix Some settings are managed by your organization. If you want some personal help, add Ishy2595 to your bnet and Ill help you diagnose it better, I am a PC Tech in a local computer shop, so ive come across a load of wierd stuff in my time. 1 and the latest servicepack Heroglyph 2. Apply to new clips: This option is. Pinnacle Studio Video Editing software is used by over 13 Million people. The final object layout button opens another pop out menu, this one concerned with object justification. Some home devices with WiFi connectivity are equipped with a signal relay function. Pick of the settings tweaks is to lower volumetric lighting quality. Geben Sie bitte Ihre Email Adresse ein. Geben Sie bitte Ihre Email Adresse ein. To test DNS resolution, attempt to ping a remote web host, such as. The Twitter clip above is.
Versions of this User Manual:
Square Enix files strange trademarks for Final Fantasy 7, Final Bar Line, and Labyrinth Striker. Registration is fast, simple, and absolutely free. Mobo also has a lot of firmwares available. Pinnacle studio version 12 movie editing windows. Other Borderlands 2 Guides: Golden Keys Explained. As soon as you install and open the utility, you will initially see the Wizard button in the application; click on it. Click Start, right click My Computer, select Properties, click Hardware tab, and click Device Manager. Keep in mind that this method is also recommended by MS specialists when it comes to mitigating the 0x0000bcb error. Dmp C:UsersHowardAppDataLocalTempWER 67922 0. Therefore, we repeat, if you are on version 2004 or older, you should upgrade to version 21H1 before 21H2 is released. All of these commands are particularly useful in menu creation, since you generally want menu buttons to be laid out in a regular fashion.
Thu 19, 2022
Unfortunately, both methods wipe the data stored on the disk. We are supported by our audience. The selected disk is of the GPT partition style. Filtering makes the ground texture crispier and the paint in the middle of the road becomes more visible. Apart, from this try the below given fixes accordingly. Convert each disk except Disk 0 to dynamic disks. Windows XPOn the Windows taskbar bottom, right, right click the Wireless Network Connection icon and select Disable. Pre Release Beliefs and Expectations –. Generic USB redirection and client drive considerations. The promise and possibilities that a title like BioShock dangles tantalisingly in front of us keeps us all hanging on in there, keeps us believing, keeps us pre ordering. The thing that strikes you instantly about BioShock and Rapture as a place is the stunning atmosphere it manages to conjure it really is quite unlike anything else in the way Irrational has managed to immerse your senses in a way you always hoped a ‘proper’ next generation title would.
You appear to have Javascript turned off Please visit your browser settings to enable Javascript
Public const int ERROR ALREADY ASSIGNED = 0x00000055; /// The specified network password is not correct. This is a free and open source video editor for Windows 11. Boot from GPT is only supported for 64 bit of Windows 7 on UEFI based systems. Our system scored P4766 points in 3DMark Vantage with 3802 GPU score and 20083 CPU score at Performance preset. We encourage XAIL members with Windows 11 to check this out and provide feedback. April 17, 2019April 17, 2019. Delete the current BCD configuration file by renaming it this will keep the old boot configuration as a backup:ren BCD BCD. Double click Network Connections, right click Local Area Network, and select Properties. Here is how you can keep your Windows 10 from upgrading to version 21H2. A large part of leveraging cloud based group policies starts with assessing your current policy landscape and determining if these policies need to move over to Workspace ONE UEM. For the sake of readers who aren’t conversant with disk partition types and installation compatibility modes, we will quickly explain the MBR and GPT types of disk partition schemes below, and provide the 4 feasible fixes for the issue of “Windows cannot be installed to the disk”. Your motherboard will contain one or the other, not both. Before you go any further, bookmark our Tiny Tina’s Wonderlands best builds to read about next. NVidia Users: any driver works, tested on 3xx and 4xx drivers. In case all the turkey talk, Black Friday mania and Christmas trees didn’t tip you off – there’s another way to know for sure the holidays. Note: Complementary to Workspace ONE AirLift, you can also leverage the Microsoft MDM Migration Analysis Tool MMAT to generate a report of which policies map to modern policies. The Global Policy is built in and cannot be deleted. Crazy to think that a Windows game would perform better in a Linux VM under Windows than running on Windows natively, even if the reason is that it’s effectively presenting the game with worse hardware that it understands how to use more effectively. TAA and FidelityFX will reduce aliasing and resharpen the game respectively, delivering a great visual result. The user can change GPT to MBR directly during the installation of the Windows operating system. The different wireless security features of your Linksys router guards your network against possible instances of hacking. It only takes a minute to sign up. 95 USD for 1 year subscription to use all the features. If you’re playing a PC game, consider switching to the Game Mode as it disables all features not required for gaming, dedicating all system resources to the game to enhance your gaming experience. For Windows 10, Go to Settings => Update and Security => Troubleshoot => Additional troubleshooters.
Using the JSON configuration
To continue this, after you installed Vista, it was critically important for you to FIRST install the Intel Chipset Software Installation Utility before any other software. 9in Box 126pc kit for 1 5 makers. The guaranteed full function support of operating systems of the Windows family, including the latest Windows 7 and Windows Server 2008 R2. We’ll find it for you. The pandemic spurred a surge in consumer use of CTV and has made it a key channel for marketers wanting to engage viewers who are moving away from linear TV. Select “Local Port” as the port type. Errors regarding unplugged network cables have several potential causes. Endorsed by over 13 million people, it allows you to create complex movie projects with modern tools like. If you encounter a similar error, here’s what you need to do. 150 Designing Games Three of Bob. Before fixing the error, it is important for us to learn why it happens. Note: Once you disable the Run command, you will not be able to launch the Run window from anywhere including using the Win + R hotkey combination, or from the Start Menu, or through Windows Search etc. Oit might have updated your drivers into oblivion. Good luck yall and have a good day.
C states
If you’re in the market for a new car, one of the first things you’ll. It shouldn’t even be a question fans have whether Pokemon following you will or will not be in each Pokemon game before release. The attacking team must battle through one sector at a time before they lose all their available respawns. Bonus: They’re currently on sale. By extension, the material quality preset itself can move from ultra down to medium too the performance boost isn’t substantial at just four per cent, but it’s enough to warrant the change. Check out these interesting ads related to “pinnacle studio”. In the Aruba user centric network, each AP has a unique name and belongs to an AP group. Celebrate this Mother’s Day with Logitech as we have picked our best products offerings for your stylish and workaholic Mom. I have been writing several articles on shortcuts keys used in various online services and software programs. The application page shows the new policy assignment. This site uses cookies to offer you a better browsing experience. There’s tons of ‘FPS fixes’ online, few help, and even then it’s barely noticeable. If the corresponding plug in is not available within EDIUS 8/9 after having installed the 64bit setups of Vitascene V3 or Herogplyph V4 then please download and install this windows component.
Most Popular Articles
To reset the text to default size;Hold down the Ctrl key Cmd on Mac and press 0 zero. Define access policies by user group and per application to increase security without compromising end user experience. If the task takes longer than that, the computer considers the graphics card frozen and attempts a recovery. For more details, see Creating Maintenance Tasks at Citrix Docs. In the ipconfig command output on the client computer, look for the IPv4 address assigned to the local computer, and the default gateway IP address. So I found this answer: How do I install Windows 8. New York state health officials found the super contagious BA. Connect the SSD using a SATA cable and correct the Boot Order in BIOS. But sometimes it just gives you generic files which still doesn’t tell you much. Fix 3: Convert to MBR Using Disk Management. The user interface of Shotcut has been translated into over 30 languages including English, Dutch, German, French, Japanese, etc. Ini files or accessing config files. Click OK to save the configuration and exit. Hi James – when you say you are trying to reinstall the Realtek Driver – what Driver are you trying to install and from where download/ original cd. NVidia Users: any driver works, tested on 3xx and 4xx drivers. Latest News: Windows 11 hacked again at Pwn2Own, Telsa Model 3 also falls. I don’t always pick up on this stuff even when half the internet seems to be baying about it, but playing through BS1R I was acutely aware that my mouse felt like it was trying to skate through jelly. The dark program window makes clip clips the center of attention, and you can switch between features such as components, clips, colors, effects, audio, and titles, as well as edit or create your own workspace, and even can pull any panel out of the program window and float it to wherever you want it to appear. Going into the game, the first big decision to make from a settings perspective is whether to run under DX11 or the experimental DX12 option.
Thread Tools
By Howard Davis, September 11, 2017 in Windows. PRICING: You can find products similar to this one for sale below. “AP Channel Assignments”. Let us know how we can make it better. The following steps show how to configure your network connection on a Windows 10 system. Don’t worry too much if you’re on team GeForce, though: we’ve been testing Borderlands 3 across a range of GPUs and CPUs, and it looks like it will run at least decently on any hardware. © 2022 Privacy Voorwaarden. Reinstalling printer ports and their drivers is a proven solution to error 0x00000bcb that can eliminate driver conflicts. You can use it to trim, split, add text to GIFs and make a GIF from a video or image. You will get a window named Restrictions saying The operation has been cancelled due to restrictions in effect on this computer. It supports hundreds of video, audio, and image formats, so you can import your media files into Shotcut without needing to convert them into popular formats. Ini file in C:UsersAppDataRoamingBioShockHDBioShock to pump options up or down, but it’s a fiddle, it’s opaque and there’s no guarantee that any of it will work well. Public const int ERROR LOCK VIOLATION = 0x00000021; /// The wrong disk is in the drive. The new editing features for new users include a combined storyboard timeline view and in app video help. I am sure you can help me. This video editing software comes with an intuitive and easy to use user interface and plenty of features. Reported daily cases in the U. Now with over 400 titles tagged and over 100 with 5 or more tags, we are excited to share players can now search and then filter by one or more tags to find their next game. Just wanted to update in case anyone else has this issue. It means press the Enter key. Now, go to the Advanced tab and tap on Printing Defaults. By default, the Firebox does not create log messages for connections that are allowed by packet filter policies such as the Ping policy.
Documentation
1 Global Weight Loss and Weight Management Diet Market Opportunities and Forecasts, 2021 2027, May 2021, alliedmarketresearch. C Copyright OCWORKBENCH 1998 2018. The editing functions include splitting, trimming, rotating, speeding up, and slowing down. Our choice is not without reason as Premiere Rush showcases features like. That was something i tried when i was crashing in path of exile. 5 full core utilization. Use these tips to get started with V Rising. The Group Policy Editor is a very handy tool in Windows 10 Professional, Enterprise and Education for controlling many advanced aspects of access and function for other users. There is an interview with Ken Levine, I believe from 2010, discussing an artist quitting after they axed the Shantytown segment because it made little sense on the context of a floating nationalist utopia. Keep in mind that this method is also recommended by MS specialists when it comes to mitigating the 0x0000bcb error. As we can see that commands can be abbreviated. 9in Box 126pc kit for 1 5 makers. A single partition of type EEh, encompassing the entire GPT drive where “entire” actually means as much of the drive as can be represented in an MBR, is indicated and identifies it as GPT. After building your report, you need to decide how you want to move your policies. When you run it, it will extract the files to a temporary directory, run the installation wizard, and remove the temporary files when the installation is complete. Although the first part proved to be repetitive after a while, Borderlands conquered the hearts of many players. Now make sure the folder Start Menu and Taskbar is selected by clicking on it. Retail unit and dollar sales from January through June 2006,” said Jeff Hastings, general manager, Pinnacle Systems. Answer: Video encoders are different than video editing application. You can use the DNS Lookup diagnostic task to test DNS name resolution from the Firebox to a host.